SOC 2 Compliance
SOC 2 Compliance
SOC 2 (Service Organization Control 2) compliance is a framework designed to ensure that service providers securely manage data to protect the interests and privacy of their clients. It’s based on the American Institute of CPAs (AICPA) Trust Service Criteria and involves an independent audit performed by a third party.
Why do we need SOC 2 Compliance?
SOC 2 Key Components:
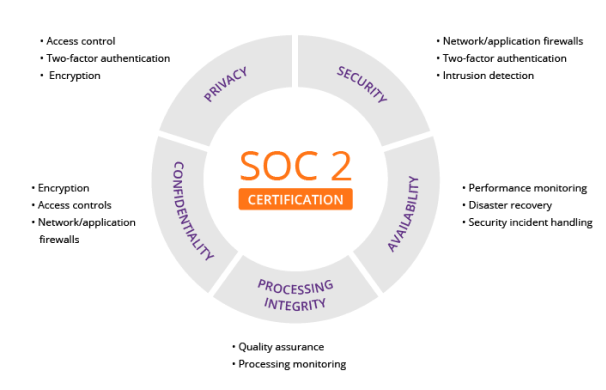
1.Trust Service Criteria (TSC): SOC 2 focuses on five criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. Companies must demonstrate adherence to these criteria in their systems and processes.
2.Audit Process: A third-party auditor evaluates the company’s systems, policies, and procedures against the Trust Service Criteria. The audit involves a deep dive into how data is handled, stored, and protected
3.Report: After the audit, a SOC 2 report is generated. There are two types: Type I reports on the description of the systems and the suitability of the design of controls, while Type II reports also assess the effectiveness of these controls over a specific period.
4.Security Measures: Companies seeking SOC 2 compliance need to implement various security measures such as access controls, encryption, monitoring, and regular risk assessments.
5.Client Assurance: SOC 2 compliance provides assurance to clients that a service provider is committed to protecting their data and operating with integrity.
6.Continuous Monitoring and Improvement: Compliance is not a one-time achievement. Companies need to continuously monitor, update, and improve their systems and processes to maintain compliance.